By Darek Kominek, P. Eng., Manager, OPC Marketing, MatrikonOPC, www.matrikonopc.com
Eric Byres, P. Eng., ISA Fellow, CTO Byres Security Inc. www.tofinosecurity.com
For the past decade, industrial control system professionals have wanted to believe that 'air gaps' truly existed between their systems and the rest of the world. They have also hoped that 'security by obscurity' would keep them safe from security threats.
Those days are over. Recent security incidents such as the game-changing Stuxnet worm are a wakeup call for the industrial automation industry. While the risk of cyber attacks and malware are no longer in doubt, the question remains, "Exactly how can an engineer reliably secure his or her control system?"
Complicating the situation is the widespread use of commercial off-the-shelf (COTS) information technologies like Windows and Ethernet on critical control systems. The use of common networking, computer and software technologies has certainly reduced costs and increased business agility. However, it has also increased the demands to balance the need for accessibility to control system data with the need to safeguard the integrity and usability of mission critical systems.
Reducing the Attack Surface
One of the most effective ways to manage the conflict between the demands of efficient access and the demands of effective security is to minimize the variety of interfaces and protocols operating between the control system and external networks. Having one approved connectivity solution serving multiple corporate requirements not only reduces administration costs, but also reduces the opportunities open to the attacker or worm. This is known as "reducing the attack surface" of a system.
Thus the key task for an administrator is to select an appropriate communications technology that can be used by the widest variety of control AND business systems. While there are a number of possible candidates, OPC is without question one of the easiest and most widespread standards to address the demands of universal data access in the industrial automation world.
Once known as OLE for Process Control, OPC is now commonly interpreted to mean Open Connectivity and the original OPC specifications are referred to as OPC Classic. OPC is the world's most widely used industrial integration standard. It's employed by a broad range of industrial and business applications ranging from interfacing human machine interface (HMI) workstations, safety instrumented systems (SIS) and DCSs on the plant floor, to enterprise databases, enterprise resource planning (ERP) systems and other business-oriented software in the corporate world.
But what about the security demands - can OPC address these? As this article will illustrate, the answer is a definite YES. By layering defenses that are OPC-aware, high security solutions can be created that meet both the security and access expectations of a company, all without administrative overload on the network or controls team. The result is a standards-based solution that has been proven across numerous control systems.
Layering Defenses: Defense in Depth
If reducing the attack surface is the first key to good security, the second is the layering of security defenses. Often referred to as 'defense in depth', the concept is to manage risk with diverse defensive strategies.
Layering defenses gives several benefits. The most obvious is that if one layer of defense is compromised, another layer of defense, using a different security method, presents an additional obstacle which can inhibit further penetration.
A more subtle, but equally powerful benefit is that attacks come in different flavors and each defensive layer can be optimized to deal with a specific range of threats.
Defense in Depth: Bank Example
Security in a bank presents a good analogy for the defense in depth approach to security for control systems. What is it that makes a typical bank more secure than a home or convenience store?
The Stuxnet worm, malware designed specifically to attack Siemens WinCC, PCS7 and S7 PLC products, enters a control system through infected USB keys (so Internet connectivity was not a requirement for infection). However once inside it spreads to other computers using protocols for file sharing, printer sharing and SQL database access.
Since there were no patches for these "attacks" when the worm was first discovered, the best defense was to not let those protocols reach critical servers unless absolutely needed. Unfortunately, as noted earlier, old fashioned OPC solutions would do just the opposite – every protocol possible was free to be sent to the OPC server, whether it was needed for control or not.
Bank doors are effective, but simple security devices. They are either locked or unlocked. They either grant or deny access to customers on an all-or-nothing basis – regardless of what a visitor looks like or how the visitor behaves.
One layer up is the security guards. They ensure that access to the bank is for people who have a legitimate need to be there and will 'behave' within expected norms. They regard each visitor based on specific criteria, such as, not wearing a mask, suspicious behavior, acting erratically etc.
At yet another level, the tellers, security box keys, passwords, etc. keep these pre-screened customers from accessing other accounts or information. Rather than worrying if a visitor should or should not be in the bank, the tellers and passwords present a different layer of security: account security. These measures 'filter' what account access individual customers are allowed, based on who they are.
Note that the security layers are context specific, which is why banks don't simply have additional security guards at every level. The security solution must fit the context of the threat expected at that level.
{pb}
Industrial Control System Security
So what does this have to do with security on the plant floor? Well, for industrial communications the roles of the 'bank guard' and the 'teller' are broadly analogous to 'Network Security' and 'Application-Focused Security'.
For example, the firewall acts like the guard, so that specified protocols are either permitted or denied access into the control network. And just like a more experienced bank guard, a more sophisticated SCADA-aware firewall observes the traffic beyond the obvious protocol types and makes additional filtering decisions based on the behavior and context of the systems using these protocols on the network.
Similarly, an OPC server with a robust OPC security implementation can act like a well-trained bank teller. After a user successfully connects to an OPC server, the OPC Security configuration ensures they only get access to the specific sets of data they are supposed to see. Attempts to access others' data should be blocked and logged.
As with the guard and the bank teller example, the firewall providing the network security and the OPC server are an essential team. For example, a firewall can block millions of randomly malformed messages directed at a server as part of a Denial of Service (DoS) attack. At the same time, user authentication and authorization checks can prevent a more subtle attacker inside the firewall (such as a disgruntled employee) from accessing process set points in a system and making changes that might risk property or lives.
Network-Focused Security
To understand network-focused security, it is important to know that most TCP/IP protocols, such as Modbus TCP, include an internationally recognized number (called a port number) in each message. This identifies the message as using a specific upper layer protocol, such as HTTP or Modbus TCP. This consistent protocol identification makes it easy for firewalls to block or allow specific messages based on function. For example, to block all Modbus TCP traffic, all a firewall needs to do is search for and then block any message that contains the number assigned to Modbus TCP (namely 502) in its TCP port field.
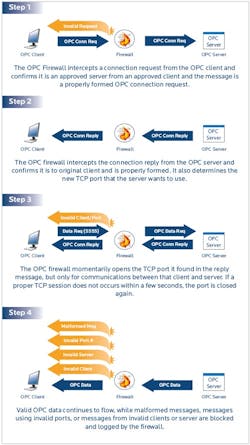
An out-of-the-box OPC server does not use a fixed TCP port number. Instead the server dynamically assigns a new TCP port number to each process that it uses to communicate with OPC Clients. The OPC clients must discover these associated port numbers by connecting to the OPC server and asking what TCP port number they should use for the session. The OPC clients then make a new TCP connection to the OPC server using the new port number.
An OPC server's ablity to designate any port between 1024 and 65535 for communications provides some ease of use advantages. Unfortunately it has also caused many IT professionals to consider OPC "firewall unfriendly" in the past. Configuring a traditional IT firewall to leave such a wide range of ports open is like having a sleeping bank security guard watch the front door. On the other hand, insisting on locking down the dynamic ports effectively ends up blocking all OPC communications.
This has changed significantly with the availability of OPC-aware firewall technology. New OPC-aware firewalls can now automatically track and manage OPC Classic's dynamic port problem. These firewalls are designed to be dropped into existing networks without any changes to existing OPC clients and servers. The OPC dynamic port issues are no longer a reason not to install firewalls in front of OPC servers.
Application-Focused Security
Returning to the bank analogy, once visitors get past the front door and the guard they approach a teller to take care of their transactions. The teller's job is to both facilitate transactions and to ensure only those accounts the visitor has access to are affected. The OPC servers of virtually all OPC vendors simply rely on DCOM (or an OPC-aware firewall) to address security (the guard at the door) and do not provide specific access control security (the tellers).
{pb}
Access control security, or application-focused security, must be addressed through OPC-specific security measures and through properly designed OPC architectures. Corporate firewalls and general Windows DCOM security are not aware of the OPC context. Only by using security products that are OPC 'aware', that support the OPC Security specification, and that properly utilize the information this provides is it possible to provide an effective level of protection.
Role and User-Focused Security
The OPC Security specification focuses on client identification by using trusted credentials to determine access authorization decisions by the OPC Server. It enables OPC products to provide specific security controls on adding, browsing, reading and/or writing individual OPC items.
Within the plant environment different job roles require different types of data access:
- Control system engineers might require full read and write access to all points in the automation system
- Operators might be restricted to only those data points associated with the status and control of machines within their particular plant unit
- Management level personnel would most certainly only require read access to key performance data items
In a less famous incident directly related to OPC Classic, a major refining complex was infected by a virus in 2009 when a contractor remotely connected to a control system to provide maintenance support. The virus was able to propagate from OPC clients to OPC servers, infecting multiple control systems in the facility and causing repeated crashes of key servers.
OPC Classic's dynamic port allocation issues complicated the problem, as it made it almost impossible to use IT firewalls to isolate one control system from another. Today, OPC-aware firewalls would have prevented the worm from spreading.
Example Solution
Combining network-focused and application-focused OPC security technologies is a tested and proven solution for industry. For network-focused security, the Tofino Security Appliance with the Tofino OPC Enforcer Loadable Software Module (www.tofinosecurity.com) can be used to secure any vendor's OPC client/server software.
Similarly, for granular role and user-based security (that is, application-focused security), the MatrikonOPC Security Gateway (www.opcsecurity.com) is fully based on the OPC Security specification. It delivers control down to the per-user-per-tag level and provides complete security for OPC architectures regardless of what vendor the OPC components are from.
These two products have been successfully tested and used together. The Tofino technology provides front line protection from 99.99% of all network based attacks (such as Denial of Service, unapproved clients, and malformed DCOM connections). Once network traffic related to OPC has been vetted, the MatrikonOPC Security Gateway enforces the specific security policies chosen by the administrator– ensuring each user only gets access to the specific data he or she has authorization to work with.
Security you can Bank on
The implications of ignoring OPC security will grow rapidly as the demand for business to control network connectivity continues to increase. History shows that the root cause behind many publicized security failures has been the result of improper use of, or the complete lack of, security safeguards.
Control automation professionals who are security aware use a combination of control system focused network security practices, proper OPC architecture design, and OPC–centric security products. Using the right products, the security of existing systems can be greatly enhanced without the need for replacing equipment or in-depth IT experience. The MatrikonOPC Security Gateway and the Tofino OPC Enforcer are off-the-shelf components that can secure OPC-based communications quickly and effectively.
The reality is that security incidents don't just happen to 'other people'. Smart companies will prepare for the unexpected by evaluating their control system security before a costly security incident occurs.
For a detailed discussion of defense in depth for OPC Security, download the companion White Paper "Effective OPC Security for Control Systems – Solutions you can bank on"
Latest from Home

Leaders relevant to this article: