What's the Best Defense Against Stuxnet?
I. INTRODUCTION
The worm initially spreads indiscriminately, but includes a highly specialized malware payload that is designed to target only Siemens SCADA systems that are configured to control and monitor specific industrial processes. Unlike most malware, Stuxnet does little harm to computers and networks that do not meet specific configuration requirements. For its targets, Stuxnet contains, among other things, code for a man-in-the-middle attack that fakes industrial process control sensor signals so an infected system does not shut down due to abnormal behavior[3].
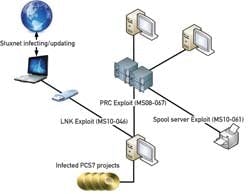
Stuxnet attacks Windows systems using an unprecedented four zero-day attacks. It is initially spread using infected removable drives such as USB flash drives, and then uses other exploits and techniques such as peer-to-peer RPC to infect and update other computers inside private networks that are not directly connected to the Internet (Fig. 1).
The Stuxnet authors stole VeriSign-issued certificates from two reputable companies: RealTek and JMicron. That is a double attack against reputation. First, it is no easy task to obtain a certificate from VeriSign. Second, there is a long history of trust in the files originating from these companies. Certificate-stealing malware is far from new, in fact, the Zeus trojan has been doing it since 2006. Malware authors have never needed to use those certificates over the years, but that is slowly changing, and Stuxnet is a proof for it. Stuxnet serves indirectly as an eye-opener to Microsoft, making the company realize that it should not allow execution of files that have tampered signatures[4].
Earlier versions of Stuxnet had been causing problems in some cases (such as downloading the program on a PLC), and no one knew what what happening. Kaspersky Lab reported the 43rd version of Stuxnet on December 23, 2011, showing that Stuxnet is still running and active.[5]
This paper compares the results of the most well-known security products for detecting Stuxnet malware and for locating infecting or suspicious files that contain Stuxnet. Section II describes the conditions of our test methodology—choosing products, their settings, using virtual machine, etc. Section III lists the included products and their versions. Section IV presents the results of each product for seven infected projects and their comparison with each other. Finally, Section V presents a summary of our conclusions.
II. TEST METHODOLOGY
Products included in this article constitute some very effective antivirus/security packs with relatively high on-demand detection rates. The participated products are selected based on some well-known independent Anti-Virus software tests/reviews, such as AV-Comparatives[6], PC Magazine[7], CNET reviews[8], Virus Bulletin[9] and Tech Media Network[10].
Figure 1. The infection begins in a USB drive and spreads to other computers inside private networks.
Our methodology has the following conditions:- Because of using last updates for all antivirus software, the operating system is installed on a virtual machine.
- The operating system is Microsoft Windows XP-SP3 that includes four zero-day patches for Stuxnet contributed by Microsoft [11].
- Each antivirus product is installed on the OS using default product settings and its related virtual machine files saved to an external hard disk.
- When the tests started, all antivirus products were updated until March 28, 2012. After that, PC was disconnected from the Internet and isolated.
- Seven infected projects were used as the set of samples for this article.
- PCS7 archived projects are very common because of their smaller capacity in comparison with the original project, making them easy to transfer. Therefore archived samples used for these tests were not extracted (retrieved).
- Samples from all sources were copied to each virtual machine.
- Infected project names were renamed to make sorting and maintenance more effective.
- The trial version of each antivirus product was used because original versions of some products are not available in my country, Iran. These products were directly downloaded from their official websites. It is necessary to mention that trial version is exactly like a commercial version, except for the time of usage.
- The name of the detected malware is really important for alerting users that their systems are infected by Stuxnet. Also the name of infected files and their roots were considered and compared.
- Most of the industrial computers are not connected to the Internet, so these tests is performed not using an active Internet connection.
III. DETECTING TESTS
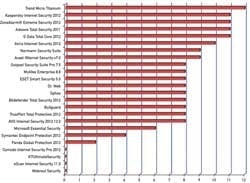
Figure 2. Each product receives a score for finding an infecting file.
The conditions for participation in our tests are listed in the Section II. The products were updated and frozen on March 28, 2012. The following 24 up-to-date products were included in these tests:- Bitdefender Total Security 2012
- AVG Internet Security 2012
- Symantec Endpoint Protection 12.1
- ESET NOD32 Smart Security 5.0.93.0
- Microsoft Essential Security 2.1.1116.0
- McAfee Virus Scan Enterprise 8.8
- Avira Antivirus Professional 10.2
- G Data Total Core 2012
- Trust Port Total Protection 2012
- Avast Internet Security v7.0
- Outpost Security Suite Pro 7.5
- Kaspersky Internet Security 2012
- Trend Micro Titanium Maximum Security 2012
- Panda Global Protection 2012
- K7 Ultimate Security 2012
- eScan Internet Security 11.0
- Adware Total Security 2011
- Norman Security Suite 16.0.0.400
- Bullgaurd 12.0.217
- Comodo Internet Security Pro 2012
- Dr. Web 7.0.0.10140
- Sophos Endpoint Security 10.0
- ZoneAlarm Extreme Security 2012
- Webroot Secure Anywhere 8.0.1.154
Nowadays, almost all products run with the highest protection settings by default; some, however, may automatically switch to the highest settings once infections begin to occur. Due to this, and in order to ensure comparable results, all products were tested with their default settings. Also, several products make use of cloud technologies, which require an active Internet connection, but as mentioned in previous section, in this test there was no Internet connection.
Here, seven infected projects named Prj-1 to Prj-7 are shown. For each project, the tests results tables containing the detection malware details of various products are listed in Table I to Table VII.
IV. RESULTS
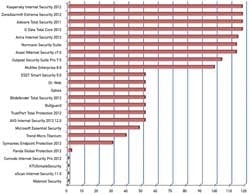
Figure 3. Here the score indicates how many pieces of malware were detected.
According to results, each product gives a different name to the malware. Despite some existing organizations such as CVE that provide a dictionary of common names for publicly known information security vulnerabilities [12], there is no unique name for each malware.Based on the results, which are listed in Table I to Table VII, the infected/infecting files are
- cc_tlg7.sav
- cc_alg.sav
- cc_tag.sav
- s7hkimdb.dll
- XR000000.MDX
- S7000001.MDX
Although there are more infecting files, like MRXCLS.sys and MRXNET.sys ([11] and [13]), those are not listed here because they exist on the infected system, and here we checked only the infected projects on a clean isolated system (see Section III). Also, based on descriptions and reports published on some web pages such as Symantec ([14], [15]), ESET[16], McAfee ([17] to [21]), Kaspersky ([22] to [26]), Trend Micro ([27], [28]) and Avira ([29] to [33]) we can say those six files certainly have Stuxnet or are created by it.
CLICK IMAGE TO ENLARGE
Name detecting test
Figure 4. This test shows which systems are
best at detecting the common names
of the malware.
On the other hand, four isolated projects were tested and none of them had the six infected/infecting files which are listed before. All infected/infecting files which are found by security products can be found on the roots below, respectively:
%ProjectRoot%/wincproj/OS/GraCS/cc_tlg7.sav
%ProjectRoot%/wincproj/OS/GraCS/cc_alg.sav
%ProjectRoot%/wincproj/OS/GraCS/cc_tag.sav
%ProjectRoot%/HOmSave7/{whatever}/s7hkimdb.dll
%ProjectRoot%/XUTILS/listen/XR000000.MDX
%ProjectRoot%/XUTILS/listen/S7000001.MDX
For comparison, three kinds of tests were performed—type-detecting test, malware counting test and name-detecting test. For the type detecting test, each product will get a score if it detects an infecting file (Fig. 2). For malware-counting test, the number of detected malware was used (Fig. 3). And in the last test, a name comparison is done because the users must know if their files are infected by Stuxnet (Fig. 4).
V. CONCLUSION
Unfortunately, none of the products can detect all various versions of the Stuxnet malware (Table I to Table VII). Our experimental results suggest that scanning each project by both Trend Micro and Kaspersky products is a good way to detect/disinfect Stuxnet, but that is not enough. It can be concluded that manually deleting is the best way to clean infected projects, but that requires having up-to-date knowledge about Stuxnet. It is worth mentioning that the XR000000.MDX file reported as an encrypted copy of Stuxnet by Trend Micro[28] but, surprisingly, surprisingly their product was not able to detect it in all infected projects until the experiment date.
REFERENCES
[1] VIRUSBLOKADA (2012, May 3).
[2] Helen Martin. (2010, November 1). Vancouver Expedition [Online].
[3] WIKIPEDIA (2012, April 15). [ONLINE].
[4] Roel Schouwenberg. ( 2010, September). Breaking the habit [Online].
[5] SECURELIST (2011, December 23). Worm.Win32.Stuxnet.ai [Online].
[6] AV-Comparatives.org
[7] Neil J. Rubenking. (2011, October 5). PC Magazine [Online].
[8] CNET Reviews
[9] Virus Bulletin
[10] Top Ten Reviews
[11] A. Matrosov, E. Rodionov, D. Harley, J. Malcho. (2011, January). Stuxnet Under Microscope [Online].
[12] Common Vlnerabilities and Exposures
[13] N. Falliere, L. O. Murchu, E. Chien, "W32.Stuxnet Dossier", Symantec Corp., Ver. 1.4, February 2011.
[14] SYMANTEC. (2010, September 17). W32.Stuxnet [Online].
[15] SYMANTEC. (2010, July 18). W32.Stuxnet!lnk [Online].
[16] ESET. (2010, July 15). Win32/Stuxnet.A [Online].
[17] MCAFEE. (2010, July 16). Stuxnet [Online].
[18] MCAFEE. (2012, March 7). Stuxnet!14E9A18DA7E7 [Online].
[19] MCAFEE. (2011, April 2). Stuxnet!2D6CEE3D0305 [Online].
[20] MCAFEE. (2010, December 27). Stuxnet!4BEE6DAC25A4 [Online].
[21] MCAFEE. (2010, December 27). Stuxnet!6E1B6DBD7348 [Online].
[22] SECURELIST. (2010, September 20). Rootkit.Win32.Stuxnet.a [Online].
[23] SECURELIST. (2010, September 20). Rootkit.Win32.Stuxnet.b [Online].
[24] SECURELIST. (2011, February 24). Worm.Win32.Stuxnet.e [Online].
[25] SECURELIST. (2011, February 24). Worm.Win32.Stuxnet.m [Online].
[26] SECURELIST. (2011, February 24). Worm.Win32.Stuxnet.a [Online].
[27] TRENDMICRO. (2010, July 22). WORM_STUXNET.SM [Online].
[28] TRENDMICRO. (2010, July 16). WORM_STUXNET.A [Online].
[29] AVIRA. (2010, November 25). TR/Drop.Stuxnet.A.40 [Online].
[30] AVIRA. (2010, July 28). TR/Drop.Stuxnet.F [Online].
[31] AVIRA. (2010, July 16). RKit/Stuxnet.A [Online].
[32] AVIRA. (2010, July 15). TR/Drop.Stuxnet.A.5 [Online].
Latest from Safety Instrumented Systems

Leaders relevant to this article: