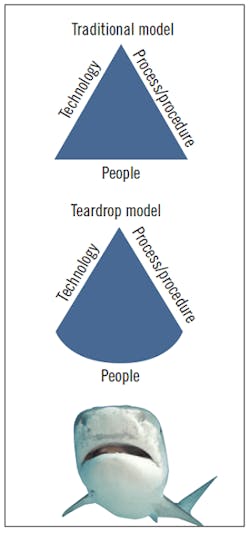
The commonly accepted information and control system cybersecurity models identify three key components to a cybersecurity defense plan or program. These include technology (technical controls), process/procedure (administrative controls), and people (the stewards, enactors or users of the controls). The history of attacks against computer-based systems, however, suggests that the triangle, with equal weighting of the three elements, may not be the most representative model for the increasingly complex cybersecurity environment. An alternate model is proposed to more realistically depict the larger attack surface and relative weakness of the people component, drawing better focus on this most vulnerable and easily exploited element of the system. The revised concept, termed the “teardrop model” of cybersecurity, illustrates the people component as a larger, bowed edge to the model shape, representing its broader and more vulnerable attack surface.
This teardrop model is proposed to help better communicate the importance of the people component in an organization’s cybersecurity plan or program. The model provides an improved visual image of the increased attack surface, and the relatively soft underbelly of the system’s people component, which is more commonly attacked than rest of the system. These people attacks have proven to be quite effective in bypassing or defeating the typically more hardened technical controls, especially when social engineering or organization-focused intelligence-gathering is used to identify prime soft targets, such as administrators or engineers, who have credentialed access and oversight of key technical controls. The human element is often neglected, although it can and should be the first area to address when trying to improve an organization’s or system’s cybersecurity. In highly effective attacks experienced during the past several years, people have been very often the first component that attackers attempt to leverage.
This soft underbelly may be the most underleveraged asset used to protect the system. It has an intrinsic, adaptable intelligence that the other controls typically lack, since most technical controls are built on fixed rule sets and rule-based algorithms that lack agility in adapting to ever-changing threat strategies and methods. In building and strengthening a cybersecurity infrastructure, the people component is often the lowest hanging fruit for tangible risk reduction, with lower capital cost and faster response time than technical controls, which require time to design, acquire and deploy. Yet, in many cases, little to no investment has been made in informing and equipping this most exposed front line of defense. This neglect would be the equivalent of an army having front-line troops in place but with no training, situational intelligence or weapons to enable defense against an attack.
To improve overall security, a series of steps or actions can be taken to transform or harden this weak spot:
Educate: Provide training to the organization based on roles. Provide general training (with testing or some form of verifying comprehension) on phishing, spearphishing, portable media use, strong password principles, and general information protection behaviors. Provide clear training on what to look out for and what to do when key events occur. Provide more intensive training for administrators and engineers who need to have a higher level of awareness, suspicion and “cyber hygiene,” including personal use of social media and the Internet. Training should include measurement of learning objectives through quizzes, case exercises or exams. Both standardized and customizable scenario-based threat awareness and action training are readily available on the market today. Incorporate cyberattack scenarios into operator training systems to simulate symptoms of control systems being compromised, and develop operator responses to the scenarios.
Equip: Prepare your “soft assets” with tools to defend the front line. First, deploy a clear and easy system to safely report phishing (email or phone) to a security response team (SRT) or security operations center (SOC) for action and analysis. Once again, technology solutions are available to aid in capture and reporting of phishing attacks. Second, provide a quick and easy method for reporting a cybersecurity incident or risk concern (by intranet, email, phone), also connected to an SOC or response team for action. For system administrators and engineers, provide technology tools to support good cyber hygiene, to manage and scan mobile media and/or computers (scrub-in and scrub-out hygiene). In best practice, provide some means to transport and inspect the data onto a previously established clean destination for transfer to/from production systems through advanced inspection and sandbox firewall technology.
Evaluate: Assess technology performance by using testing tools, including (safe) test phishing and spearphishing email, and portable media “bait” (USBs, SSDs, DVD/CD, etc.). Once again, several tools are available to assist with generation and response conditioning (training) of test and bait recipients. Establish periodic (irregularly timed) audits and testing of portable media and computer use on development and production systems. Evaluate operator responses in training scenarios. Where simulation training systems exist, test operators on their responses to attack scenarios such as remote access takeover, DDoS, frozen data, or process anomalies symptomatic of control outputs operating independently of measurements. Consider use of red/blue team exercises to tabletop attacks and response actions. Gather metrics on performance, and provide immediate response coaching through the test media to provide necessary feedback on erroneous actions.
Reinforce: Continue to provide the training for new personnel, with periodic refresher instruction. Combine training and initiate re-training with test results. A best-practice system allows follow-up conversations with personnel who are experiencing difficulty detecting or properly responding to test cases, going a human step beyond automatic corrective action or refresher training. Provide recognition and reward for individuals who demonstrate acuity in recognizimg threats, and respond proactively as “intelligent sensors” to identify threats and security concerns within the organization. Continue to inform the organization about their target status to maintain awareness and vigilance.
The intent of the teardrop model is to raise awareness of the importance of the people component of an organization’s or system’s cybersecurity model, and that it’s important to recognize it is both a common vulnerability and an often undervalued, unleveraged asset. People can be a front-line vigilance and intelligence asset if properly engaged, equipped and empowered. Cyber attackers use human creativity to find ways to deceive, impersonate or hijack personnel to gain inside access to cyber assets. Human intuition is often the best defense against such ploys and attacks, but that intuition must be awakened, informed, equipped and motivated to be transformed from a defense liability to a defense asset.
Latest from Cybersecurity

Leaders relevant to this article: