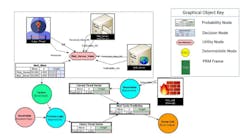
Forecasting where a hacker will go once inside an OT network
Work is ongoing in identifying cyber threats, vulnerabilities and locating hacker penetration in electric utility and other operational technology (OT) networks. However, existing technologies including Intrusion Detection Systems, Intrusion Prevention Systems, Security Information and Event Management and Security Orchestration, Automation and Response can’t predict the future movement of a cyber intrusion that has successfully breached the OT network.
Under U.S. Air Force and Department of Energy (DOE) contracts, the Global Center for Advanced Studies and its subcontractors, Lockheed Martin, Applied Control Solutions, Carnegie Mellon University and Georgia Tech, have developed a prototype modeling approach to forecast a cyber threat’s future maneuvers in compromised OT networks – the Cyber Attack Forecasting Systems (CAFS). The approach is based on techniques used by the DoD for ballistic missile attack warning and assessment, including probabilistic multi-model filters and multi-hypothesis method within a Bayesian framework.
This technology became critical as the DOE-sponsored literature search found that the most recent and comprehensive work on cyberattack forecasting was by Iranian researchers.
If interested in learning more, please contact Dr. Tom Savell at [email protected] or me at [email protected].
About the Author
Joe Weiss
Cybersecurity Contributor
Joe Weiss P.E., CISM, is managing partner of Applied Control Solutions, LLC, in Cupertino, CA. Formerly of KEMA and EPRI, Joe is an international authority on cybersecurity. You can contact him at [email protected]