The RSA Cybersecurity Conference is not relevant to control systems – what’s missing is in plain sight
I helped start the control system cybersecurity program for the electric utilities in 2000 while at the Electric Power Research Institute (EPRI). At that time, the RSA Cybersecurity Conference was in San Jose and was primarily a cryptography conference. I attended a number of those early conferences and realized that since many control systems and control system field devices such as process sensors, actuators and drives couldn’t handle cryptography, the conference wasn’t relevant to most control systems and control system field devices.
In 2006, Gartner coined the term “operational technology” (OT) which shifted the focus from control system field devices owned by the engineering organizations to OT networks owned by the network security organizations. With that change, the control system field devices that have no cybersecurity, authentication, or cyber forensics and where you “go boom in the night” were orphaned from cybersecurity programs and the OT networks became the focus of cybersecurity programs and the RSA Cybersecurity Conference.
2025 Conference
This year’s RSA Cybersecurity Conference was held April 28th-May 1st and was billed as the world’s largest cybersecurity conference. The RSA Cybersecurity Conference is a network security conference and includes both IT and OT network subjects. This year’s RSA Cybersecurity Conference focused on anything called artificial intelligence (AI), whether in IT or OT. There were numerous discussions about network cybersecurity threats from Russia, China, and Iran, as well as on the latest advanced persistent threats. There were sessions on the latest network cyber vulnerabilities and network cyberattacks. There were panel sessions and presentations on OT and critical infrastructures.
But there weren’t any discussions about cybersecurity issues of control system field devices. Additionally, there were no discussions about control system cyber incidents, whether malicious or unintentional. However, control system cyber incidents can’t be hidden – lights go off, pipelines rupture, toxic chemicals are released, trains crash, planes crash, ships crash, water systems are compromised, food processing is impacted, etc. These incidents are just not identified as being cyber-related but “glitches” as there are no cyber forensics or appropriate training.
There were discussions about Chinese “typhoon” cyberattacks but no discussions of hardware backdoors in large Chinese-made electric power transformers that bypassed the OT networks. This control system cybersecurity gap included a presentation given by the director of cyber information sharing for the Food and Ag-ISAC who warned not only of the increase in ransomware incidents but the continued lack of visibility into the full scope of the problem.
“A lot of it never gets reported, so a ransomware attack happens, and we never get the full details,” he told Recorded Future News on the sidelines of the conference. “I wish companies would be more open in talking about it and sharing ‘Here's what they use, here's how we fixed it,’ so the rest of us can prevent that.”
There were many “floor discussions” about the Apr. 28, 2025, Spanish power outage thinking it may have been due to a cyberattack (not the case).
Food and Ag control system cyber attack
According to court documents filed Apr. 16, 2025, in August 2023, a former employee of a poultry cleaning service altered levels of peracetic acid and sodium hydroxide at a poultry processing facility while disabling safety alarms and redirecting notification emails to mask his actions. On May 2, 2025, Food Safety News published an article about the August 2023 hack. Even a single incident of food industry tampering could raise consumer concerns, such as the Tylenol tampering case did many years ago. This was a significant hack of a manufacturing process, yet there was no mention of this control system cyberattack at the RSA Cybersecurity Conference.
Get your subscription to Control's tri-weekly newsletter.
Food and Ag facilities lack control system cybersecurity
Poultry plants, like water systems, power plants, oil/gas, etc., increasingly rely on remote automated control systems. In this case, the control system used for chemical dosing (sanitation) was monitored and controlled via internet-connected platforms.
On Mar. 15, 2016, I gave the keynote at the Food Industry Cybersecurity Summit in Washington D.C. discussing real control system cyber incidents and getting “new” actual cases from the attendees. Yet there are still few discussions about Food and Ag sector control system cybersecurity. Moreover, the Food and Ag sector has no cybersecurity requirements for the control systems used in the food manufacturing process (Food Safety Modernization Act).
Consequently, on Mar. 14, 2021, I issued a blog on the lack of control system cybersecurity in the food and agriculture industries. In June 2024, the Office of Director of National Intelligence identified Iranian control system cyberattacks against multiple U.S. food and beverage facilities. The USDA and FDA have yet to issue specific control system cybersecurity mandates for food manufacturing and processing plants, leaving the industry to self-regulate. Given the recent job cuts at FDA, there will be fewer people to monitor food manufacturing processing facilities and possibly more “insider threats”.
Summary
There have been more than 17 million malicious and unintentional control system cyber incidents across all sectors globally that have killed more than 30,000 people. The vast majority were not identified as being cyber-related, but “glitches” as they were not Internet Protocol network-related incidents.
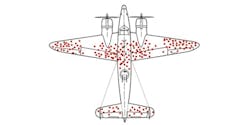
We should reflect on the learnings of Dr. Abraham Wald from 1943 and “truly try our best to see what’s not there” – what is missing in plain sight. Wald looked at the damaged portions of returning planes that showed locations where they sustained damage and were still able to return to base; those hit in other places presumedly did not survive and therefore were not addressed.
Russia, China, and Iran are aware of the cybersecurity gaps between OT networks and control system field devices. Consequently, they are exploiting these gaps knowing the cyber defenders are not looking there. As a result, we need appropriate control system cybersecurity training for both the network and engineering/operations organizations to identify when control system incidents are cyber-related.
About the Author
Joe Weiss
Cybersecurity Contributor
Joe Weiss P.E., CISM, is managing partner of Applied Control Solutions, LLC, in Cupertino, CA. Formerly of KEMA and EPRI, Joe is an international authority on cybersecurity. You can contact him at [email protected]