Multiple choices
The many flavors of Ethernet and wireless are trendy, But its the underlying acceptance and adoption of fieldbuses that pushes users to find some tasty and unexpected applications.
Is there life beyond Ethernet and wirelwess? Maybe, but dont hold your breath. For now, these two overarching technologies and their various incarnations, sub-derivatives, and combinations seem likely to dominate the future of industrial networkingor dominate talk about itat least for now.
Of course, their combined presence is still estimated at only two-thirds to three-quarters of the total industrial networking installed base, consisting mostly of 4-20 mA and other point-to-point hardwiring methods, even though fieldbuses have made inroads and steady increases for years. However, few observers seem to doubt the overall direction they believe networking is inexorably going to take.
So, why does everyone think Ethernet and wireless are taking over the industrial networking world, even though they havent conquered too much of it yet? Two words: (lots of) momentum and (a little) misperception. Ethernets overwhelming presence in office/business settings has long fueled expectations it will take over the plant-floor, too. If possible, the hype surrounding wireless is even more intense based on the huge savings and easy installation its supposed to deliver. Theyre sort of like Yahoo! and Google, until YouTube and whatevers next comes along. Everybody loves a winner and dominances comforting familiarity, until they get bored and root for the underdog and the novelty of a little upheavalbut not too much.
COTS Cultivates Creativity
Distorted distractions aside, there might be an undercurrent fueling much of the buzz about Ethernet and wireless. Some observers say a critical mass of mainstream users finally is accepting the idea that non-proprietary, twisted-pair fieldbuses, Ethernet, the Internet, and wireless are practical networking methods, and that numerous users are implementing them. Not surprisingly, a rapid influx of users with unique applications and requirements may be sparking a renaissance in innovations, hybrid and combined networks, and an equally unprecedented era of networking creativity and diversity.
Mainstream manufacturing control, automation, and networking technologies long have been used to operate large entertainment stage structures and amusement park rides, as well as some engineers Halloween and Christmas displays. These and similar non-manufacturing applications are only multiplying faster as open, non-proprietary networks gain ground.
The British Airways London Eye observation wheel uses two DeviceNet networks to control its 800-passenger boarding platform.
In addition, non-traditional networking doesnt always mean replacing one network with another. Users increasingly are installing new networks on top of old ones, allowing them to operate side by side or in tandem. For instance, wireless often is used to monitor its hardwired predecessors.
In fact, the new Boeing 787 and Airbus 380 aircraft now both use Ethernet in their onboard communications and avionics control systems, but they still added their own proprietary protocols on top of Ethernet, says Brad Booth, president of the Ethernet Alliance. This is pretty compelling proof that Ethernet is as robust as any other physical-layer technology. Ethernets presence is growing in industrial networking precisely because users want these non-proprietary and COTS communications.
Ethernet Everywhere
While some trends have to be dug out and pieced together like clues in a detective story or pottery at an archeological dig, others just bop you on the head like a toddler with a rattle. For example, drive-time commuters and other radio listeners to WXRT 93.1 in the Chicago area on Nov. 15 heard a short ad from Home Depot offering contractors 1,000-ft. boxes of Cat 5e cable for $89. Pretty unremarkable until you realize that the copywriter and retailer didnt even mention they were selling Ethernet cable because they assumed everyone already knows what it is! That is serious momentum. Can PLC sales at Starbucks along with lattes, biscotti, and CDs be far behind?
Booth reports that Ethernet now has approximately 500 million nodes operating worldwide, and adds that three IEEE 802.3 Ethernet standards updates were approved this year: 10 GBaseT, 10 GBaseLRM for multi-mode fiberoptics, and a frame expansion to help Ethernet data packets improve security. Ethernet also is the only consistent, pluggable, powered network, adds Booth. Power over Ethernet (PoE) can even use special RJ45 connectors that plug into a socket to power other devices. Its now able to transmit 13 W DC, and 30 W DC is now under development, too. PoE is about four years old, and is used to power a variety of devices such as IP-based telephones.
Booth adds that a 100-Gbps Ethernet standard and its Energy-Efficient Ethernet project are both in early development. This effort will try to give Ethernet users the ability to change data rates, and affect the power their networks draw. Theyre expected to be able to push up to 100 Gbps when needed, and ramp down when activity is low, potentally saving tremendous amounts of power.
The real utilization of Ethernet is starting to make an impact, says Fred Cohn, president of Modbus-IDA and Schneider Electrics U.S. marketing director. Were seeing Ethernet grow in traditional applications such as large automotive plants. However, were also seeing Ethernet moving out closer to the ends of some applications, devices, I/O points, and connections.
However, despite its attractions, the journey to Ethernet implementation can be harder than it looks. We used to have bullet-proof proprietary networks that handled time-critical interlocks and shared real-time control data, or dedicated, reliable fieldbuses that were isolated from the corporate side, says Mark Hoffman, president of Automation & Control Concepts Inc., a system integrator in St. Louis. Now we have many companies struggling with the move from proprietary networks to Ethernet via wired and wireless, and increasing conflicts between IT departments and plant-floor engineers. Many of these networks arent sufficiently separated, and so office systems are hampering plant operations. One client recently was trying to set up remote management for 20 manufacturing locations, and had to call someplace in China to get the IP addresses they needed.
As a result, Hoffman advises network users to create separate virtual local area networks (VLANs) for their plant-floor and office networks; deploy routing rules that move messages to one side of this fence or the other; and then link these VLANs only by a secure firewall. He adds that users also should create committees that define PC specifications for plant-floor applications, so they only get the software and hardware they really need, and define rules for networking procedures, updates, and backups.
Ethernet isnt exactly the point. The key issue is using the IP suite, especially UDP/IP, as the basis for communications in industrial environments and the derivations of public protocols based on that communications suite, says Alex Johnson, system architect at Invensys Process Systems. The use of IP-based protocols enables our industry to take advantage of the commercial infrastructure created to support that type of communications. On top of IP, you find a similar set of standards based on web protocols and standards, for example, XML and SOAP. OPC UA and PRODML are probably the most well-known. In general, I think the biggest change is the apparent commitment to using standard, commercial protocols to implement communications. Its this change that will bring real value. Its not really the medium that matters. The use of these protocols allows the selection of the appropriate mediummicroware, copper, fiber, wireless, etc.for the application. One can argue that any protocol that isnt IP-based, and any medium that cant carry it easily, are going to eventually go away. Of course, that wont happen overnight. There are so many issues. For example, no one is going to yank out their HART transmitters or Foundation fieldbus H1 transmitters in the near term. However, I believe that eventually we will be talking to field devices using IP.
SP100 Wireless Battle?
Though wireless applications are multiplying in parallel to Ethernet, there appears to be a conflict brewing over wireless standards. Wireless mostly has been governed by an evolving alphabet of IEEE 802.11x standards, and ISAs SP100 committee has been working to determine which methods are best for industrial networking in process control applications. However, these efforts now are coalescing around two wireless methods, whose supporters/suppliers seem to be squaring off against each other.
One camp is Wireless Networking for Secure Industrial Applications (WNSIA), which supports frequency-hopping, spread-spectrum (FHSS) wireless, and reportedly a more point-to-point methodology. The other group is called Collaboration Initiaive (CI), and its members advocate direct-sequence, spread-spectrum (DSSS) wireless, and a more mesh-oriented strategy.
From a user perspective, this is sort of Ford versus Chevy. Both of these technologies work well, says Hesh Kagan, president of the Wireless Industrial Networking Alliance (WINA) and Invensys Process Systems technology marketing director. They just have different perspectives. Were trying to bring these camps together right now. SP100 is still scheduled to release its pre-standard in 2007.
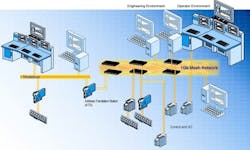
It seems the main trend is to continue to move to common commercial standards such as the IP suite over various media, adds Johnson. The wireless battle is just beginning, the various 802.1x standards and derivatives will play a part, but its not obvious that they will be the only solution. Users are finding that adopting commercial technologies that use commercial intelligent switches and commercial fiberoptic hardware components have made it possible to meet their ever-increasing bandwidth and performance requirements in a secure, reliable, and cost-effective manner. For example, the only proprietary technology used in our mesh control network is the software that provides intelligent routing between our I/A Series system stations and the mesh (See Figure 2 below) to help ensure non-stop communications.
FIGURE 2: A FINE MESHGene Chen, product manager for Honeywells wireless network, adds, As with most emerging technologies, todays market offers proprietary, wireless-enabled solutions that tactically solve industrial business needs, but might not meet requirements for the future. Key implementation issues that must be addressed include handling multiple types of devices from just a few to a thousand, operating in a noisy RF environment, sending data reliably, good device power management, and solid, simple security. Many industrial facilities already are deploying wireless networks for targeted requirements, but they also need to consider the future. For example, functionality, reliability, security, power management, scalability, sensor support, control loop support, actuator support, and 802.11 WiFi support all play a role in future plant expansion. Wireless networks that dont address each area may not fit long-term strategic use.
OPCs New Worlds
Not content to rest on its interoperability progress, the OPC Foundation plans to follow the 2006 release of its OPC Unified Architecture (OPC-UA) with an even more far-reaching project early in 2007. Tom Burke, OPC Foundations president, says the organization has been working with Microsoft and Sun Microsystems to develop OPC-UA Universal Discovery protocol, and plans to release it in the next three to four months. Based on web services, Universal Plug-and-Play, and Universal Device Discovery Interface concepts, this new discovery protocol is expected improve OPCs plug-and-play functions beyond its connecting capabilities.
This isnt just connecting. This is connecting and being able to find out much more about the device youre connected to, says Burke. Many end-users cant communicate with and understand their existing components and systems. This will allow them to find out about all the systems out there, and do discoveries independent of the system theyre running on. This means users can find out whats on all the computers theyre connected to, and scroll down through a list of all their programs. So, when you plug a PLC in through this protocol, it will automatically provide the information other devices will need. For example, if you have a sensor on a door, youll not only be able to know when its open or closed, but can find out who opened it and get their complete authorization.
IT Taking Over?
One slightly ominous trend is that some IT departments are becoming more responsible for process controls and automation. Where most IT staffs traditionally were responsible for specific servers, PCs, and corporate intranets, the influence and jurisdiction of some appears to be expanding as controls mix with Internet-based technologies and as corporate-level users want to see more real-time manufacturing data. In fact, because IT ends up controlling the specs for PCs and PC-based controls, some controls engineers are ending up working for their IT departments.
There can be problems when IT takes over because they might think its okay to take down a network at midnight, even though its not okay because an application is running, explains Hoffman. IT also might send a virus update to plant-floor devices that dont need them, even though telling a machine to do a virus scan could lock it up. Unnecessary shutdowns like this have been increasing over the past three or four years. A lot of IT people now are getting those 3 a.m. calls, and regret taking over plant-floor systems.
Doug Brenner, principal engineer at Superior Controls, a system integrator in Plaistow, N.H., adds that, IT traditionally owns the corporate Ethernet network. In the past we typically installed a separate network for controls. Now companies can have one physical network, and use port filtering to allow ports on a switch to be grouped into separate logical networks. So, for example, theres a separate logical network that supports PLC communications to SCADA nodes. In our experience, any critical I/O communication such as Ethernet/IP still is separate. Its the operator interface and monitoring network that can now be reliably integrated into the corporate network.
Likewise, IT managers usually own the network, server room, corporate standard servers, and desktops. Because IT also owns information processing, it becomes more involved as increasing value is put on information and integration, even if IT doesnt own factory automation.
Then all the MES stuff is integration between ERP and process automation, which is a natural for IT, adds Brenner. A confluence of 21 CFR Part 11, Sarbanes Oxley, and similar types of requirements beg for centralized data management. You even could argue that 21 CFR Part 11 really is all about IT requirements for process automation. In addition, some of Superiors customers can view read-only HMI screens anywhere, anytime over a VPN. Network filtering is used to restrict access to the servers from which changes can be made.
In places where IT doesnt own process automation, relationships with IT are either very cooperative or still are evolving, Brenner says. We work with one large company where the IT infrastructure is good and the network is solid, the IT people are very service oriented, and we work closely with an Oracle DBA. At another large company, where the relationship is still evolving, were installing software, but one thing that makes it difficult is that we dont have control over the network and SQL Server database, and IT support isnt readily available. There are a lot of projects that are easier and more reasonable to do when a solid network is already in place.
One positive change resulting from using corporate networks and IT involvement, says Brenner, is the ability to use a corporate domain user name and password for security. In the past they had sites with system-specific individual user names and passwords.
Introspective Networking
If you want to build an industrial network, there are a few basic questions you need to ask yourself before you get started. These can focus your search, and help you implement the most appropriate network for your application.
- Whats your primary reason for establishing or renovating your industrial network? Define what you need to accomplish.
- What are your topology requirements? What physical dimension and layout does your network need to have?
- How small can you go? Can you experiment with a smaller network first and grow as you go? Or do you need a large network and immediate help from a system integrator?
- What are the speed and data-size requirements of your information application? How often do you need to scan your system? Do you need small data packets delivered quickly, or does your application need to process larger data chunks slowly?
- How are you going to secure and provide power? Do you need to run more wiring? Can you use batteries or even Power over Ethernet (PoE)?
- Do you need a hardwired, 4-20 mA, point-to-point network, or can you use a twisted-pair fieldbus, Ethernet flavor, wireless, or Internet-based strategy?
- Does your application need a combination of networks? It might be useful to ask yourself the first question again here.
- What about connector uniformity and other accompanying hardware issues? Is the chosen configuration simple and reusable? What support and system integration services are available locally, and how soon can they get here if needed?