ISA-99 Is THE Big Deal for 21st Century Plants
Read Charlie Gifford's blog... Hitchhiking Through Manufacturing
In October 2007, the ISA-99 Committee approved a ground-breaking standard, ANSI/ISA99.00.012007, Security for Industrial Automation and Control Systems, Part 1, and a technical report, ANSI/ISA-TR99.00.01-2007, Security Technologies for Industrial Automation and Control Systems. According to a 2007 AMR Research report on corporate IT spending by 1,000 manufacturing companies, 19% of their budgets were directed at manufacturing operations management (MOM) systems and their enterprise integration, up from 3% in 2001. Thats an increase of over 600% in six years! This spending addresses the need for manufacturing plants to become more adaptive to a companys transition to a globally distributed network of supply chains.
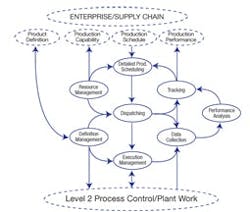
These new manufacturing operations systems have to provide production capability and performance information to many enterprise and supply systems and even to suppliers and customers in a context of outsourced production. This all makes for a proliferation of unsecured interfaces into and out of the plant.
Your plant-floor/IT security system will have to take into account all the data exchanges between systems that take place. This drawing shows only part of the system. Similar exchanges take place in the maintenance, quality and inventory departments, and each interface can be vulnerable.
Here is the developing issue. Eighty percent or more MOM systems are selected, designed, maintained and owned by a corporate IT department. The corporate IT groups are going through some hard lessons about the life-cycle support of high-change MOM systems that have to execute the continually changing workflows and business processes for production. Their focus is on supporting functionality, not on securing the plant from outside threats.
ISA-95, Enterprise-to-Control Integration, Standard, Part 1 defines over 60 primary data exchanges. Part 3, Activity Models of MOM, shows over 20 exchanges for each of the four activity models, which add up to a few hundred interfaces between production, quality, maintenance, inventory and labor operations systems.
As we build the real-time enterprise for the global market, we also are building some real-time time bombs, thanks to the lack of awareness and general plant-floor experience within the corporate IT departments. I am not against centralizing systems or applications, and I do believe that it can be done and should be done in some circumstances, but little or no attention is paid to doing the real risk analysis of such an approach.
How do I know this? Because in responding to more than 70 multi-plant requests-for-proposals for MOM systems globally, I have yet to see ISA-99 recommendations specified. Yes, governmental bodies are specifying ISA-99 for hazardous chemical, oil and gas, and nuclear production facilities, but not for most of the large batch or discrete industries.
Manufacturing cybersecurity outside of the process industries is simply an afterthought, if it is thought of at all, presenting a huge national security risk that no one is noticing.
Time was, most MOM systems were either paper-based, isolated systems with simple flat-file interfaces or spreadsheet applications. Cyberthreats were few because there werent enough opportunities to bother with.
Now corporate IT departments are putting a big electronic pipe into the plant and centralizing process and safety-critical applications in data centers. Unfortunately, the IT groups do not have knowledge to deal with the dynamic nature and rate of change of MOM systems and their mostly customized, proliferating interfaces and reports. People who are not now, nor ever have been on the ground at the plant are making workflow decisions about safety and product, creating a golden opportunity for cyberattackers.
To get the attention IT and corporate management, go to the link below and print out Section 4 of ISA-99. Then hand it to IT and corporate management AND YELL LOUDLY AT THEM TO WAKE UP!
For more details on Section 4, go to www.controlglobal.com/0804_Hitchhiker.html.