Key to effectively managing industry’s next-generation digital field will be a unified approach to device integration and cybersecurity that is aligned industrywide. FieldComm Group already is active in the development of both, and the Group’s HART, FDI and PA-DIM standards will all play a role in reaching this important goal.
More than 30 years ago, the original HART was created as a command/response protocol superimposed on the 4-20mA analog signal used by electronic instruments to communicate process variable and control instructions between host control systems and field instruments. To manage those communications, each host and client needed an address, as defined in the original HART specification.
Fast forward to 2007, when HART was adapted to Internet Protocol (IP) over Ethernet to backhaul data from WirelessHART gateways (itself inherently secure), the addressing scheme defined by HART was no longer required. Rather, IP-addressing was used, and HART-IP was born. And while Ethernet and IP represent much of what’s good in the networking world, IP-addressable devices also come with the need to address potential cybersecurity concerns.
HART communications secured
So, with the 2020 revision 7.7 of the HART specifications, requirements for always-on security suites are now specified to provide communication security, audit logs and syslogging. These measures are designed to secure not onlyinstrument communications via WirelessHART gateways and the new breed of gateways that extract HART data from analog loops, but also to the new generation of Ethernet-APL instruments poised to extend HART-IP all the way to the field instruments themselves.
HART-IP communication security requires that new devices support the industry standard Internet Protocol Transport Layer Security (TLS) and Datagram Transport Layer Security (DTLS) suites. HART commands have been added to simplify security deployment and aid users in navigating multiple security options. Additional diagnostics and forensic requirements are also included.
Devices also are required to capture audit logs that summarize communications activities, including records such as client identification, connection start/stop times and whether the device configuration was changed in that session.
Finally, HART-IP devices must support syslogging, an industry standard means of publishing device events to a network’s security information and event management (SIEM) system. All HART-IP devices must support network time using either Network Time Protocol (NTP) or Precision Time Protocol (PTP). Consequently, all syslog messages from all network devices are time synchronized, enabling forensics on network-wide behavior and activities.
Combining communication security, audit logs and syslogging results in robust security for HART-IP enabled products that doesn’t stop at the plant’s fence line. Add appropriate firewalls, together with data diodes to ensure outside instrument data access is read-only, and HART-IP can successfully transition to remote enterprise servers or cloud-based applications.
Device integration solved
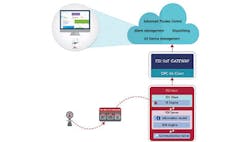
And while HART-IP addresses the problem of device data security from the field to the cloud, other FieldComm Group technologies and standards, notably FDI and PA-DIM, help solve the problem of integrating field device information across the broader range of network protocols, host devices and other applications that will interact with them over their entire lifecycle, including for tasks such as device configuration, replacement and maintenance. This also includes Industrial IoT gateways for delivering data to cloud-based monitoring, diagnostics and analytics applications (Figure).
In FDI technology, there are two parts to the system: the field side (Device Package) and the host side (Server). On the field side, a device’s specific software and documentation are encapsulated into its FDI Device Package. On the host side, the FDI Server imports the FDI Device Package and hosts the FDI Information Model, which is accessible by any FDI or generic OPC UA Client application. In this way, FDI Industrial IoT gateways are able to fetch device information from the FDI Information Model via OPC UA Services and publish it to the cloud for further processing. This enables any enterprise application to access field data for business operations.
Information modeled
At the level of Industrial IoT and related cloud applications, OPC UA has emerged as the preferred information modeling framework—not only for process instruments and associated data but for many other industrial assets as well. The FieldComm Group’s Process Automation Device Information Model, or PA-DIM, is only one of several dozen OPC Companion Specifications that describe the functions and data flows of equipment ranging from compressed air systems to machine tools.
But OPC UA does more than just information modeling. More broadly speaking it’s described as an interoperability standard for the secure and reliable exchange of data in the industrial automation space and in other industries, ensuring the seamless flow of information among devices from multiple vendors. Included in the OPC UA framework are its own “extensible” communication and security mechanisms, which means it’s designed so that innovative new technologies and methodologies such as new transport protocols, security algorithms, encoding standards, or application-services can be
incorporated into OPC UA while maintaining backwards compatibility for existing products.
FDI technology is already tied to OPC UA through its device information model, which can be mapped to PA-DIM, which is also based on OPC UA. Further out, FieldComm Group is developing concepts for a NexGen field instrument technology that would extend not only Ethernet to the field level, but the OPC UA architecture as well. Ultimately, HART, along with other protocols developed specifically for industry may be reinvented once again, this time as as information models that guide the converged IT/OT data architectures of tomorrow.