When it comes to cybersecurity during the COVID-19 pandemic, what's works at work can also work at home.
All of the useful cybersecurity hygiene practices, antivirus and intrusion detection software, network segmentation and protection, traffic monitoring and anomaly detection, and other cybersecurity tools used in businesses and on plant floors can be extended to remote and residential users. Plus, ongoing digital transformation efforts and more designed/baked-in cybersecurity are making it simpler for many users and their organizations to add and maintain protections, which makes it more likely they'll be implemented and used consistently.
"There are three main tasks for anyone trying to get in. They start by learning about their target from all kinds of publicly available information. Even a job listing that asks for SCADA or I/O expertise can make a target easier to penetrate. Plus, there's even more on social media, so we're trying learn what to publish, and control what information goes out or comes back in," says Ashok Patel, global network architect at Owens Corning in Toledo, Ohio, who co-presented "Defending systems against sophisticated attacks" at ARC Advisory Group's Industry Forum 2020 in Orlando earlier this year. "The second task is ways to get in. Three to five years ago, we thought perimeter devices and firewalls were enough, but lately networks need more protection. For example, one of our engineers recently developed a server in Amazon Web Services (AWS), but didn't put the firewall on it, and its logging function later starting getting up to 200 hits per second on its one Internet protocol (IP) address. We didn't even think it was up and running, but the local area network (LAN) turned out to be connected. The cybersecurity staff said they don't connect anything until it's ready, and it changed what we do, too."
Sonny Miller, electrical services and SCADA supervisor at Rancho California Water District, adds, "In the past 18 months, we increased our cybersecurity by updating passwords and adding firewalls to our PLCs and SCADA system; tested and adopted web-based Ignition SCADA software to allow more flexibility; got some basic training on Internet protocol (IP) addressing for our Modbus devices and packet-level networking; and added cybersecurity to our weekly safety meetings."
Rancho California operates approximately 45 wells, 30 pump stations and 35 reservoirs to provide primarily portable water to about 150,000 residents in Temecula and Murrieta, Calif., and runs a wastewater treatment plant that provides recycled water mostly for irrigation.
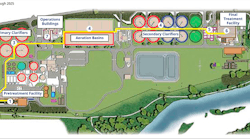
Figure 1: To give its staff mobile access to onsite controls at its wastewater treatment plant that processes 277 million gallons per day, the City of Eugene, Ore., worked with Yokogawa to develop a secure wireless network by segregating its business, wireless and process networks, implementing centralized antivirus software, patch management and backup/recovery, and integrating according to the IEC 62443 cybersecurity standards. Source: City of Eugene and Yokogawa
"My system administrator and I also got Certified SCADA Security Architect (CSSA) training and certifications from the InfoSec Institute, and work more with our front-end IT staff on remote SCADA, hired and outside service to do a penetration test (pen test), and did some risk/resilience testing by having the U.S. Environmental Protection Agency (EPA) evaluate our documentation," says Miller. "We try to stay on top of cybersecurity, but 'we don't know what we don't know.' A new technology could also mean a new threat, so we learn what we can from the U.S. Dept. of Homeland Security, the FBI and InfoSec, and if they tell us there's a vulnerability in our firmware, we update it. If we can be proactive, and there's a breach by a person or software code, then we'll have a defense plan and solution in place that's beyond what a typical hacker is willing to spend. So far, our testing indicates we're ahead."
Begin with basics and buy-in
Effective cybersecurity starts with essential tasks like turning on or removing default passwords, segmenting networks with firewalls and monitoring network traffic, but several other steps are needed to get the ball rolling and keep it moving, according to Matt Malone, industrial control system (ICS) cybersecurity consultant at Yokogawa Corp. of America.
"The first three steps include: establish a cross-functional team with peers from different departments such as process control, health safety and environment (HSE) and physical/site security; secure upper-management buy-in, which is easier now because cybersecurity has matured enough to become a board-level concern; and conduct an organization-wide cybersecurity risk assessment (RA) with a layers of protection analysis (LOPA), perform a passive network scan to see what's going on, find unmanaged connections, and guide a wire-walk of the facility," says Malone. "There are many options on the cybersecurity menu, but we have to remind clients not to eat everything on it all at once. Cybersecurity is a long and continuously evolving road."
Figure 2: Though usually referred to as one standard, ISA/IEC 62443 is actually a group of cybersecurity standards for industrial automation control systems (IACS), which are in various stages of development by the International Society of Automation's ISA99 committee, and recently adopted by the International Electrochemical Commission. Source: ISA
For instance, Malone reports the wastewater division of the City of Eugene, Ore., wanted to give its operators and maintenance staff mobile access to its onsite control system, which processes 277 million gallons per day, and asked its control supplier, Yokogawa, to conduct a site survey, identify optimal access points, and develop a dedicated, secure wireless network with 100% coverage and no access loss (Figure 1). Its cybersecurity aspects include: segregating its business domain, wireless area and process control network; implementing centralized antivirus software, patch management, and backup and recovery; and integrating according to the IEC 62443 standard, which provides a flexible framework to address and mitigate current and future security vulnerabilities in industrial automation and control systems (IACS) (Figure 2). It also adopted Yokogawa's VTS Portal software for secure remote access, and more flexible and efficiency monitoring and operations via its wireless network.
"Following IEC 62443 meant buying and sweating out the document's details, such as where to set nodes and learning what encryption the access points needed," explains Malone. "The risk and site assessments let us unravel many unknowns, turn over rocks in the network to find creepy-crawly problems, and gain the knowledge required to create a plan, including a hit list for the one to three years. Not much of this is sexy, but it made the wireless network at Eugene's wastewater plant more secure by eliminating weak or shared passwords, and hardening its system by eliminating default settings, disabling auto-run programs, and locking out USB ports. The best cybersecurity bang for the buck is implementing basic system hardening services, which can be done after any DCS project during planned or unplanned downtime. That, and cybersecurity risk assessments, will allow users to stay one step ahead of most intrusions and or attacks."
The International Society of Automation's various cybersecurity-related initiatives have multiplied over the years, and because "you can't tell the players without a program," here's a reminder of who does what:
- ISA Global Cybersecurity Alliance is a collaborative, open-membership forum to advance cybersecurity awareness, education and certification, readiness and knowledge-sharing to bring the automation cybersecurity ecosystem together to lead culture change, expand development and use of industry standards, and advocate sensible approaches with world governments and regulatory bodies.
- The ISA Security Compliance Institute (ISCI, www.isasecure.org) provides market awareness, technical support, education and compliance for ISASecure industrial automation control systems (IACS) and their security requirements based on ISA99 and other IACS security standards. The ISASecure designation is earned by suppliers for products that demonstrate adherence to industry-consensus cybersecurity specifications for security characteristics and supplier development practices. ISASecure is based on the IAC security lifecycle defined in ISA/IEC 62443.
- The Linking the Oil and Gas Industry to Improve Cybersecurity (LOGIIC) program is an ongoing collaboration of oil and natural gas companies and the U.S. Dept. of Homeland Security's Science and Technology Directorate. LOGIIC undertakes collaborative research and development projects to improve the level of cybersecurity in critical systems of interest to the oil and natural gas sector. The objective is to promote the interests of the sector while maintaining impartiality, the independence of the participants, and vendor neutrality.
- ISA100 Wireless is an open, universal IPv6 wireless network protocol (IEC 62734) that extends existing operations, enables new applications, breakdown protocol barriers and establishes the Industrial Internet of Things (IIoT), but it also provides robust, multi-tiered, policy-based security to ensure system operations safety. Communications are protected using time-enhanced application of the NIST standard 128-bit Advanced Encryption Standard (AES) block cipher. Its secure-key derivation method enables a trusted relationship that makes ISA100 Wireless networks secure throughout system lifecycles.