Key Highlights
- External forces such as pandemics and geopolitical conflicts significantly increase cybersecurity vulnerabilities and attack surfaces.
- Budget constraints on agencies like CISA may reduce threat intelligence and response capabilities, impacting overall network security.
- Regulations like the EU's CRA and NIS2 are driving global compliance efforts, influencing strategies beyond Europe.
While it’s all well and good to change default passwords, segment networks and monitor data traffic for anomalies, sometimes a user or organization’s individual cybersecurity efforts are impacted by larger, external forces. For instance, distancing required by COVID-19 spurred remote work, which increased networks connections and vulnerabilities to cyber-probes, -intrusions and -attacks. Likewise, the wars in Ukraine and Gaza fueled digitalized cyber-attacks on local participants, which have spilled over regionally and worldwide. Now, pointless federal funding turmoil is threatening the ability of U.S. agencies to help users protect themselves, even as Europe ramps up new cybersecurity requirements.
“Budget cuts to groups like the U.S. Dept. of Homeland Security’s Cybersecurity and Infrastructure Security Agency are having an indirect impact on network security. It’s quite likely that, as those groups recalibrate to operate with less funding, there will be less threat intelligence until someone else steps in to close the gap, or until they find ways to effectively do more with less,” says Alexandre Peixoto, cybersecurity business director for Emerson’s Process Systems and Solutions business. “For us, the two major areas CISA provides a lot of help are the CIS Benchmarks and vulnerability coordinated disclosures, which may be impacted by budget cuts, and will impact the process control and automation market.”
Peixoto reports that another situation with local and potentially global impact is the Cyber Resilience Act (CRA), a regulation coming into effect in the European Union (EU) in two stages: Phase 1 in September 2026 and Phase 2 in December 2027. Manufacturers are quickly shifting focus to ensure their products can be certified to comply with CRA because no suppliers can afford to ignore the EU marketplace.
Similarly, the EU’s updated Network and Information Security (NIS2) directive is directly impacting end users. It’s already in effect, but not all EU member states have implemented local laws, which is delaying overall adoption and enforcement. With those laws in place, service providers are helping users meet the new standards and requirements.
Emerson doesn’t believe CRA and NIS2 will be strictly applied in the EU only because multinational companies with headquarters or large presences in Europe will want to ensure consistency when working with automation vendors. Consequently, the reach of CRA and NIS2’s regulatory compliance is likely to go beyond the EU’s frontiers, and directly impact strategy and policy development. Plus, even companies that aren’t operating in the EU may find their countries adopting similar regulations in the future, so many are preparing to meet those challenges, according to Peixoto.
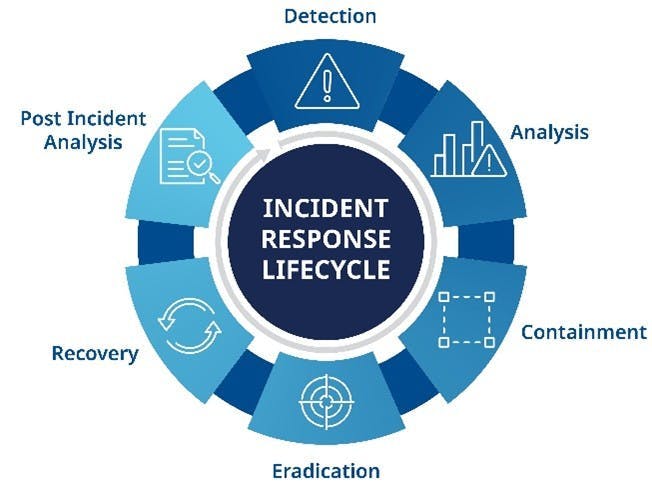
“While laws and regulations are compelling reasons for shifting and improving cybersecurity postures, more companies are simply reacting to the cybersecurity events they see happening day-to-day,” adds Peixoto. “People no longer need to look hard to find an example of industrial sites experiencing cybersecurity breaches—the days of security by obscurity have ended. Companies must be vigilant, and vigilance means going beyond the low-hanging fruit. Having just a firewall and antivirus is no longer enough. Companies need to start moving to the next level. That means starting a journey toward continuous cybersecurity improvement.” (Figure 1)
Refocus on people, technology and processes
Peixoto reports that operations technology (OT) often still sees cybersecurity as cost without direct return on the investment made.
“Nobody ever bought a cybersecurity solution because they knew it would deliver 10% more production after installation. Yet we still have cybersecurity leaders in the OT space who are innovative and who are leading by example. Why is that?” he asks. “It’s because in recent years those companies spent time and effort bridging the OT/IT gap. These teams know they need to do more with less, and to find ways to assist and upskill the less experienced and more transient personnel. That means being able to move data seamlessly from the intelligent field, through the edge, and into the cloud. It’s all part of a boundless automation strategy, but it also requires a secure foundation on which to operate.” (Figure 2)
Peixoto adds that practical cybersecurity solutions requires going back to the original cybersecurity triad—people, technology, and processes. However, each piece of that triad is subject to pitfalls. Experienced staffers are harder to come by than ever, and teams need to implement solutions that make cybersecurity intuitive for users, so they aren’t fighting against them.
“There are many opportunities in the cybersecurity space, and companies are capitalizing on it. Some are doing a great job, while others are promising much more than they can deliver” Peixoto. “OT teams need expert guidance, not just to filter out the least effective solutions, but also to ensure anything they implement will play well with their existing automation infrastructure, and bring value across the full lifecycle.”
Delek simulates a ransomware attack
For instance, one of Emerson’s customers connected people, processes, and technology to identify gaps in its cybersecurity architecture, and fix them in a practical way. Delek US is an energy and infrastructure company, which started its initiative years ago in its information technology (IT) space, and recently carried it over to OT to help ensure effective, end-to-end cybersecurity strategies and preparedness.
To put their ideas into action, Delek’s leaders engineered a tabletop exercise in a hypothetical and non-intrusive setting to simulate a cyber-attack, and test how their security technologies and response plans would work under fire. Much like a fire drill, about 75 key personnel from every level in the company, from the C-suite to the legal department to the factory floor, worked with Emerson and Delek’s incident-response partner. Together, they simulated a ransomware attack in real time, played their roles following published policies, and identified potential gaps in their response plans, and validated the thorough work that Delek already done.
Get your subscription to Control's tri-weekly newsletter.
At the heart of the project was Delek’s desire to not only have a response plan, but to be sure it was effective. Its team knew a plan created in a vacuum would have far more gaps than one that was thoroughly tested. At the end of the experiment, the Delek team knew its personnel would better understand their roles, and any missed steps would be immediately obvious, so they could be fixed more easily. Communication lines and collaboration would be improved, critical resources would be verified, and response time would shorten.
“Delek’s exercise was a resounding success. We went through the whole process with everyone following their guidebooks over the course of a four-hour exercise with stakeholders co-located in different parts of Delek in the U.S. to simulate a real-life event as closely to reality as possible,” says Peixoto. “Even beyond the lessons learned and the gaps closed, having so many people invested and working together drove home the importance of cybersecure operation to the company’s entire staff, and connected every element of the people, technology and processes in the cybersecurity triad.”
You can do cybersecurity, too
Peixoto encourages other users and companies to follow Delek’s example, and get their people involved in similar cybersecurity simulations and projects.
“First and foremost, you need an answer for the people element of the triad. Teams need to make sure they have staffing up to speed, whether it’s internal or external,” explains Peixoto. “Teams should also ensure they have the right processes in place. They shouldn’t only build or enhance what they have, but also test it continually as Delek does.
“Meanwhile, the technology element needs to be more than the search for a magic bullet. Cybersecurity technology implementation will always be a journey. That’s true for people, processes, and technology, but it’s easiest to forget when evaluating technology. Teams must continually measure their cybersecurity posture, set goals, and explore modern technologies that will help them meet those goals. It’s also equally important to do this in close collaboration with their automation provider to ensure they’re implementing solutions appropriate for their automation infrastructure.”
Reach for the device level and the future
Beyond protecting primary processes and networks, Peixoto adds that users and organizations must seek to shield sensors and other device-level components, and make sure the same is done for cloud-computing connections and services.
“It’s not just sensors. The extreme end of the automation is where there isn’t much technology to ensure protection. Lots of technology in the field is old and uses insecure communication protocols. The most important steps are physically protecting the assets and preventing access to the environment’” explains Peixoto. “However,environment. But a modernization strategy for transitioning to technologies using more secure communication is also essential. Protecting islands of automation using legacy controls will always be a problem. Modernization is effective but takes time. Until that can be accomplished, isolating and air gapping those less secure elements to the greatest extent possible is critical.”
In the future, Peixoto reports that monitoring for cybersecurity will continue to increase. In addition, security services providers are starting to talk more about cloud-connected, threat-detection technologies. What used to be antivirus is now endpoint detection and response, as well as extended detection and responses tied to threat intelligence.
“Those technologies, much like artificial intelligence (AI) will require massive data collection,” concludes Peixoto. “Companies are training those solutions today, and in the near future, some of the biggest players will unleash some powerful, aggressive technologies that have been trained on massive data stores. That will be a game changer—even more so when combined with powerful AI engines that can anticipate the moves of hackers.”
How is network security likely to evolve in the future?
Monitoring will continue to increase. In addition, security services providers are starting to talk more about cloud-connected threat detection technologies. What used to be antivirus is now endpoint detection and response and extended detection and response tied to threat intelligence. Those technologies, much like AI, will require massive data collection. Companies are training those solutions today, and in the near future, some of the biggest players are going to unleash some powerful, aggressive technologies that have been trained on massive data stores. That will be a game changer—even more so when combined with powerful AI engines that can anticipate the moves of hackers.
About the Author

Leaders relevant to this article: